Role-based access control (RBAC) is a widely used mechanism for managing permissions. It is popular for the simplicity it offers in managing user permissions based on users' roles within your organization. VGS customers who have long benefited from an organization-level RBAC have asked for fine-grained access control to their vaults.
I’m happy to share that VGS now allows vault-level access control and management of user roles, enabling customers to control access to each of their vaults within an organization. This premium feature is now generally available to all customers on the enterprise tier of VGS Vault.
How Do Vault-level Permissions Work?
Before diving deep into vault permissions, let’s look at what’s changed regarding Organization RBAC. Three roles, namely, read, write, and admin, have now been merged into two default user roles: "Admin" and “Member”. Admin has full administrative access to the entire organization and its resources. Member is basically a team member who can actively work on Organization resources, including Organization Member Vaults, with permission to create new resources.
Vault permissions are now grouped into the following roles:
- Read – This is the lowest access level. Users with this permission get view access to vault settings and routes. Examples of users with this role are non-code contributors who would want to view the list of vault routes or their logs.
- Write – This role grants users write access to vault settings and routes. The role is ideal for active contributors who can make changes to your vault routes.
- Admin – The Admin role grants full administrative access to a vault and its routes, including permissions to delete the vault and its routes. A Vault Admin can manage vault preferences as well as vault users.
Below are a few helpful examples of how vault permissions work.
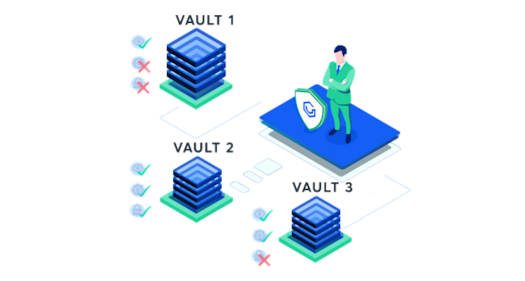
01. Organization Members With Read/Write/Admin Vault Role Can Access Only the Vaults They Have Been Granted Access To
To try out this scenario, start with your VGS Organization and add at least two users and two vaults. Now you should be able to add a new user or change an existing user’s permissions (as the example shows) to assign specific permissions on each vault. Wait until permissions are updated. Next, open the VGS dashboard in an incognito window, log in as a second user (whose rights you were editing), and see the vaults you have access to.

02. Organization Members with Read Vault Role Cannot Manage Routes
The prerequisites listed above also apply to this scenario. Now, when editing your second user’s permissions, assign a Read role on the preferred vault. Go to the incognito screen, access the VGS Dashboard, and log in as a second user and see whether you can manage routes. The Manage button should be missing now, giving you no ability to edit routes or access your route configuration.

03. Organization Members with Write/Read Vault Roles Cannot Manage Vault Settings
In this scenario, once you change your second user’s permissions to Read and Write for specific vaults, the Vault Settings page will not be viewable. Access will be restricted to access credentials, mTLS certificates, CNames, and Advanced Preferences.

Here is the full list of what one can do within the Organization and its vaults.
What Should You Take Into Account When Using Fine-grained Vault Access Control?
As a best-practice, you should manage access to resources using the principle of least privilege. This means that every role should be carefully chosen with a user’s duties in mind and based on specific actions you want to enable for that user. Bearing this principle in mind, establish clear roles for your new users and revise your existing users' roles. Use the new definitions of vault-level roles and the detailed list of permissions to get clarity on a user’s role. After implementation, establish a review cycle that periodically confirms the validity of each role. It’s also a good practice to check your users' last login activity and enforce password changes every 90 days. RBAC is only as good as its proper management and governance.
To Sum Up
The flexibility to assign granular permissions on vaults should now give you extra controls around your users' access to vault, separation of sandbox from live vaults, as well as isolation of activities among your team.
For more information or questions on this feature, please reach out to our product team at product@verygoodsecurity.com and we’ll help you out.